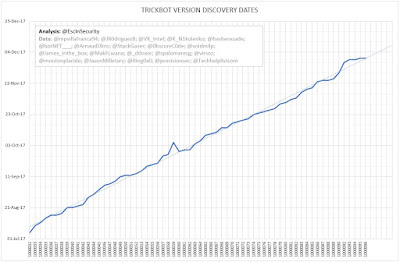
The following graph shows the rate of discovery of TrickBot versions in the wild, based on shared mcconfs. (Note: The flatter the line, the more frequently versions are discovered.)
Six versions were discovered in the last week (1000021, 1000106, 1000107, 1000108, 1000109, and 1000022), four the week before, and five the week before that. Two of the versions discovered have early version numbers (1000021 and 1000022) but only include new C2 servers. While my data does not include these versions from their 'first use', it seems these version numbers are being re-purposed in new campaigns, identified by group tags beginning 'solinger'.
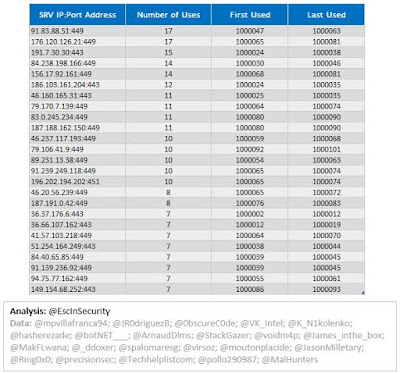
The following graph shows the number of server entries using ports:
- 443 (HTTPS);
- 445 (IBM AS Server Mapper) -- INACTIVE;
- 449 (Cray Network Semaphore Server); and
- 451 (SMB) -- INACTIVE.
The following map shows the geographical location of 80 (those scanned by Shodan) of the 90 IP addresses used in the analysed week's configs. Six of the 80 are MikroTik devices. Of the remainder, 51 are running OpenSSH, 44 are running nginx, 12 are running Apache, six are running Exim, two are running ProFTP, one is running Postfix, one is running MySQL, and one is running Haproxy http proxy -- with some servers running as many as four of these products.
The following table shows the BGP allocations of C2 servers' IP addresses to country by TrickBot version.
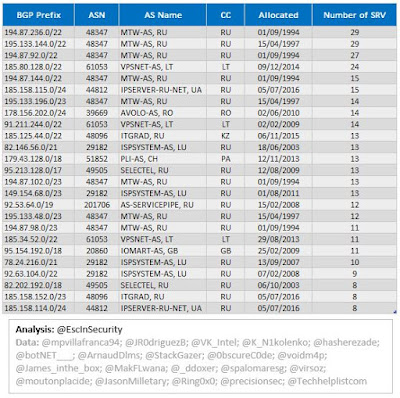
Finally, the following table shows the top 25 BGP prefixes used by TrickBot for C2 servers.
Thanks to @mpvillafranca94, @JR0driguezB, @0bscureC0de, @virsoz, @spalomaresg, @VK_Intel, @K_N1kolenko, @hasherezade, @botNET___, @ArnaudDlms, @StackGazer, @voidm4p, @James_inthe_box, @MakFLwana, @_ddoxer, @moutonplacide, @JasonMilletary,@Ring0x0, @precisionsec, @Techhelplistcom, @pollo290987, @MalHunters and @coldshell for sharing the mcconfs.
Thanks to @mpvillafranca94, @JR0driguezB, @0bscureC0de, @virsoz, @spalomaresg, @VK_Intel, @K_N1kolenko, @hasherezade, @botNET___, @ArnaudDlms, @StackGazer, @voidm4p, @James_inthe_box, @MakFLwana, @_ddoxer, @moutonplacide, @JasonMilletary,@Ring0x0, @precisionsec, @Techhelplistcom, @pollo290987, @MalHunters and @coldshell for sharing the mcconfs.