Background:
Since its first use from approximately 19th October 2016, TrickBot has frequently issued new versions of its XML configuration file, mcconf. Originally there was a single chain of config versions which started at 1000002. (There may have been a 1000001 but it is not been shared publicly.) I refer to this original sequence as iteration A. On 16th November 2017 TrickBot mcconfs were issued for older version numbers than the current iteration A configs, but with different command and control (C2) servers to those in that version's iteration A config. This indicated the start of iteration B, a new sequence of configs believed to be for a second botnet. While there is a small amount of overlap of the C2 servers between iteration A and iteration B, the majority of C2 servers are specific to an iteration (hence botnet). The iteration B botnet stopped receiving new configs on 28th February 2018. As of 28th March 2018 another iteration, iteration C, was started, once again repeating previously used version numbers but with different C2 server lists. Victim hosts in that third botnet were merged into the iteration A botnet as of 23rd May 2018.
This week's analysis:
Figure 1 shows the rate of discovery of TrickBot versions in the wild, based on shared mcconfs. The flatter the line, the more frequently versions are discovered. Ignore the two long, almost vertical lines which coincide with the switch from one iteration to the next. These vertical lines are purely an artefact of graphing the data in a single series. (Note: Full size versions of all the graphs and tables are available via the link at the end of this post.)
There were three new config versions discovered in the week commencing 18th June 2018 (A-1000212, 1000213, and A-1000214), two the week before, and four the week before that. All new config versions extend the iteration A botnet, taking this to 1000214. The secondary, iteration B, botnet was not extended in the discovered versions and remains unchanged since 1000068 of 28th February 2018. The tertiary, iteration C, botnet was merged into the iteration A botnet on 23rd May 2018.
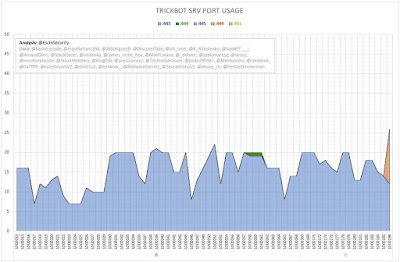
The following graphs (Figures 2 and 3) show the number of server entries using ports:
- 443 (HTTPS);
- 444 (Simple Network Paging Protocol) -- INACTIVE;
- 445 (IBM AS Server Mapper) -- INACTIVE;
- 449 (Cray Network Semaphore Server); and
- 451 (SMB) -- INACTIVE.
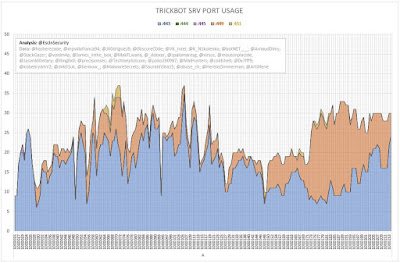 |
| Figure 2 - TrickBot SRV Port Usage (Iteration A) |
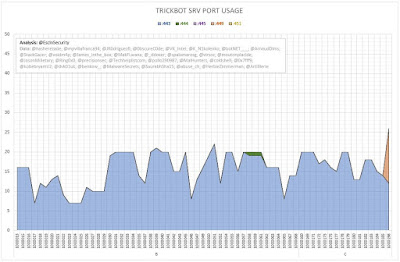 |
| Figure 3 - TrickBot SRV Port Usage (Iterations B and C) |
 |
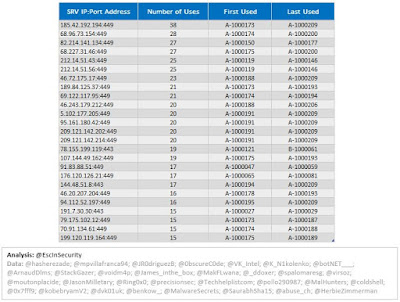
| Figure 4 - TrickBot Top 25 SRV |
 |
| Figure 6 - TrickBot Weekly Advertised SRV Count and Churn |
 |
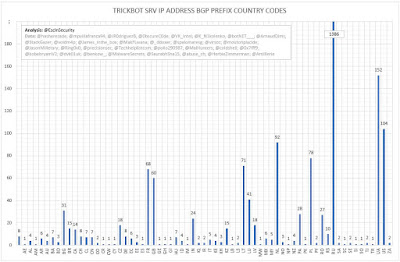
| Figure 7 - TrickBot SRV IP Address BGP Prefix Country Codes |
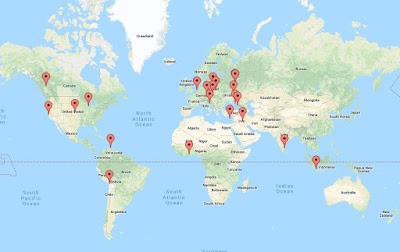
Figure 8 shows the geographical location of 45 (those with location data) of 45 (scanned by Shodan) of the 50 C2 server IP addresses used in the analysed configs.
According to Shodan's most recent data:
Figure 9 shows the BGP allocations of C2 servers' IP addresses to country by TrickBot version. (Once again, I know it's unreadable - it's just here as a placeholder. A full size version is available in the downloadable zip file at the bottom of the post.)
According to Shodan's most recent data:
- 13 are Ubiquiti devices and 11 are MikroTik devices.
- 22 are running nginx, 14 are running Dropbear SSH, 12 are running OpenSSH, seven are running Apache, five are running Exim, two are running MySQL, two are running ProFTP, one is running Postfix, and one is running VNC.
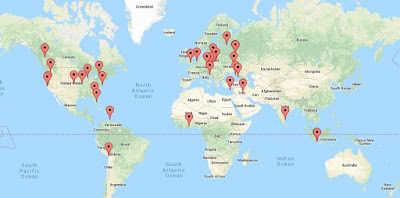 |
| Figure 8 - TrickBot C2 Server IP Locations For New Configs |
| Figure 9 - TrickBot SRV IP Address BGP Prefix Country Codes By Version |
Finally, Figure 10 shows the top 25 BGP prefixes used by TrickBot for C2 servers.
Full size versions of the figures included in this post are available here. I've also created a page documenting the various discrepancies identified in TrickBot's mcconf files.
Thanks to hasherezade, mpvillafranca94, JR0driguezB, 0bscureC0de, VK_Intel, K_N1kolenko, botNET___, ArnaudDlms, StackGazer, voidm4p, James_inthe_box, MakFLwana, _ddoxer, spalomaresg, virsoz, moutonplacide, JasonMilletary, Ring0x0, precisionsec, Techhelplistcom, pollo290987, MalHunters, coldshell, 0x7fff9, kobebryamV2, dvk01uk, benkow_, MalwareSecrets, SaurabhSha15, abuse_ch, HerbieZimmerman, and Artilllerie.
 |
| Figure 10 - TrickBot Top 25 BGP Prefixes |
Thanks to hasherezade, mpvillafranca94, JR0driguezB, 0bscureC0de, VK_Intel, K_N1kolenko, botNET___, ArnaudDlms, StackGazer, voidm4p, James_inthe_box, MakFLwana, _ddoxer, spalomaresg, virsoz, moutonplacide, JasonMilletary, Ring0x0, precisionsec, Techhelplistcom, pollo290987, MalHunters, coldshell, 0x7fff9, kobebryamV2, dvk01uk, benkow_, MalwareSecrets, SaurabhSha15, abuse_ch, HerbieZimmerman, and Artilllerie.