The following graph shows the rate of discovery of TrickBot versions in the wild, based on shared mcconfs. (Note: The flatter the line, the more frequently versions are discovered.) Full size versions of all the graphs and tables are available via the link at the end of this post.
Six new versions were discovered in the week commencing 9th April 2018 (A-1000170, A-1000171, A-1000172, A-1000173, A-1000174, and A-1000175), seven the week before, and six the week before that. All six of the discovered versions extend the original iteration of version numbers (which I refer to as iteration A), taking this to 1000175. The secondary botnet, which is reusing earlier version numbers, was not extended in the discovered versions and remains unchanged for six weeks. (I track these as part of a new, distinct iteration, iteration B, of the version numbers.)
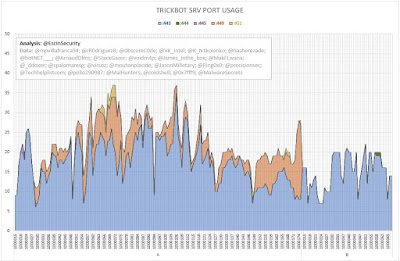
The following graph shows the number of server entries using ports:
- 443 (HTTPS);
- 444 (Simple Network Paging Protocol) -- INACTIVE;
- 445 (IBM AS Server Mapper) -- INACTIVE;
- 449 (Cray Network Semaphore Server); and
- 451 (SMB).
The following map shows the geographical location of 46 (those with location data) of 47 (scanned by Shodan) of the 58 C2 servers used in the analysed configs.
According to Shodan's most recent data:
The following table shows the BGP allocations of C2 servers' IP addresses to country by TrickBot version.
According to Shodan's most recent data:
- 14 are Ubiquiti devices and six are MikroTik devices.
- 13 are running OpenSSH, 13 are running Dropbear SSH, 12 are running nginx, four are running Exim, three are running Apache, one is running IIS, and one is running Pro FTP.
Finally, the following table shows the top 25 BGP prefixes used by TrickBot for C2 servers.
Full size versions of the images included in this post are available here.
Thanks to @mpvillafranca94, @JR0driguezB, @0bscureC0de, @virsoz, @spalomaresg, @VK_Intel, @K_N1kolenko, @hasherezade, @botNET___, @ArnaudDlms, @StackGazer,@voidm4p, @James_inthe_box, @MakFLwana, @_ddoxer, @moutonplacide, @JasonMilletary,@Ring0x0, @precisionsec, @Techhelplistcom, @pollo290987, @MalHunters, @coldshell, @0x7fff9 and @MalwareSecrets for sharing the mcconfs.
Thanks to @mpvillafranca94, @JR0driguezB, @0bscureC0de, @virsoz, @spalomaresg, @VK_Intel, @K_N1kolenko, @hasherezade, @botNET___, @ArnaudDlms, @StackGazer,@voidm4p, @James_inthe_box, @MakFLwana, @_ddoxer, @moutonplacide, @JasonMilletary,@Ring0x0, @precisionsec, @Techhelplistcom, @pollo290987, @MalHunters, @coldshell, @0x7fff9 and @MalwareSecrets for sharing the mcconfs.