Here are the results of my analysis of TrickBot Banking Trojan mcconfs shared up to the end of the
week commencing 13th November 2017. This analysis covers
818 unique C2 IP addresses used in
184 mcconfs across
73 versions, with a
latest version of 1000089.
The following graph shows the rate of discovery of TrickBot versions in the wild, based on shared mcconfs. (Note: The flatter the line, the more frequently versions are discovered.)
Four new versions discovered in the last week (1000086, 1000087, 1000088 and 1000089), three the week before, and four the week before that.
The following graph shows the number of server entries using ports:
- 443 (HTTPS);
- 445 (IBM AS Server Mapper);
- 449 (Cray Network Semaphore Server); and
- 451 (SMB).
Counts of server entries dropped briefly in 1000087 before continuing to rise. The percentage of :449 hosts is falling.
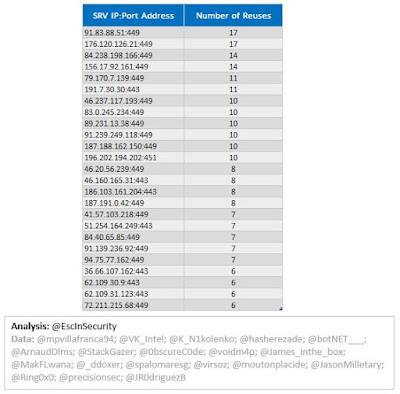
The following table shows the top 25 servers (of 818 unique) used within the 73 versions. last week's mcconfs used 67 unique servers with none used prior to 1000080 (which was discovered 31st October 2017).
The following table shows the breakdown of detected TrickBot campaign 'gtag' (group tags) values used in the 184 mcconfs analysed. The 'kas' gtag continues to be the most active campaign amongst shared mcconfs.
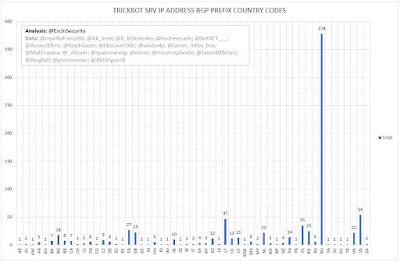
The BGP prefix registrations for the C2 server IP address are heavily biased to RU. New IPs allocated to 37xRU, 11xLT, 3xKZ, 3xNL, 2xGB, 1xCH, 1xLU.
The following table the BGP allocations of C2 servers' IP addresses to country by TrickBot version.
Thanks to
@mpvillafranca94,
@VK_Intel,
@K_N1kolenko,
@hasherezade,
@botNET___,
@ArnaudDlms,
@StackGazer,
@0bscureC0de,
@voidm4p,
@James_inthe_box,
@MakFLwana,
@_ddoxer,
@spalomaresg,
@virsoz,
@moutonplacide,
@JasonMilletary,
@Ring0x0,
@precisionsec, and
@JR0driguezB
for sharing the mcconfs.