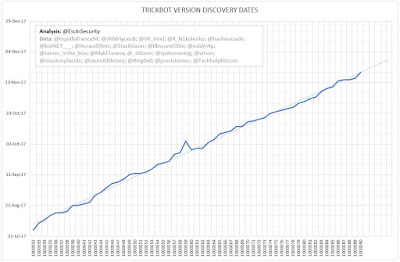
The following graph shows the rate of discovery of TrickBot versions in the wild, based on shared mcconfs. (Note: The flatter the line, the more frequently versions are discovered.)
One new versions discovered in the last week (1000090), four the week before, and three the week before that.
The following graph shows the number of server entries using ports:
- 443 (HTTPS);
- 445 (IBM AS Server Mapper);
- 449 (Cray Network Semaphore Server); and
- 451 (SMB).
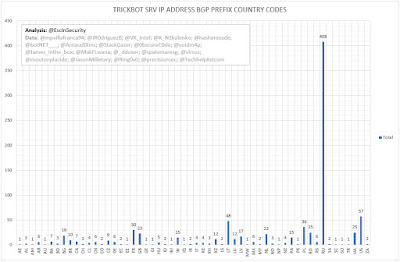
The following table the BGP allocations of C2 servers' IP addresses to country by TrickBot version.
Thanks to
@mpvillafranca94,
@JR0driguezB,
@VK_Intel,
@K_N1kolenko,
@hasherezade,
@botNET___,
@ArnaudDlms,
@StackGazer,
@0bscureC0de,
@voidm4p,
@James_inthe_box,
@MakFLwana,
@_ddoxer,
@spalomaresg,
@virsoz,
@moutonplacide,
@JasonMilletary,
@Ring0x0,
@precisionsec, and
@Techhelplistcom
for sharing the mcconfs.
Particular thanks go to @JR0driguezB for providing some old mcconfs which filled historical gaps.
Particular thanks go to @JR0driguezB for providing some old mcconfs which filled historical gaps.